
FedRAMP Built a Modern Foundation in FY25 to Deliver Massive Improvements in FY26
September 30, 2025
FedRAMP was a program operating in crisis at the beginning of FY25. Final authorization times were exceeding one year and at times approaching up to two years, the Joint Authorization Board (JAB) had shut down unexpectedly for nearly a year, years of promises for automation had failed to come to fruition, and only a little more than 350 cloud services had completed FedRAMP in 13 years. The goals, structure, and intent of the program of the first twelve years had just been rescinded and replaced by OMB Memorandum M-24-15 “Modernizing FedRAMP” without a clear path to achieve the updated vision and scope outlined in the new policy.
“We’re kind of in limbo right now on FedRAMP, and I think that’s not a good place to be. We want to get on with the implementation of the law we passed… we’ve got to make sure it’s implemented and that it achieves the goals we set for it.”
- Congressman Gerry Connolly, July 11, 2024
“The Administration created a bottleneck in this vital process, however, when it chose to shut down an existing FedRAMP authorization pathway before putting in place an alternative solution. What’s more, GSA left in limbo cloud service providers (CSPs) who invested time and resources in the now-defunct authorization process. Ultimately, unnecessarily delayed authorizations may reduce availability of cloud products and services to agencies.”
- Congresswoman Nancy Mace, September 26, 2024
“FedRAMP has failed to reduce the duplication of efforts by commercial cloud providers to provide services to the federal government as it often takes 12 to 18 months for a new product review and 4 to 12 months for a Significant Change Request… there is a conflict between the commercial market and the ability for the federal government to obtain current software.”
- Business Software Alliance, December 20, 2023
“It is critical that government and CSPs develop new approaches to FedRAMP that account for the increasing pace of innovation. The current, retroactive FedRAMP review process will continue to fail to scale with increased demand and increased functionality.”
- The Cloud Service Provider Advisory Board, December 22, 2023
“The FedRAMP process is a resource-intensive process for both CSPs and agencies interested in consuming the cloud services. Given the costs, many agencies find it difficult to sponsor one or more new cloud services each year. In fact, there are several agencies that do not sponsor any of the cloud services they consume; instead, when looking at cloud services, they rely on the work done by other departments and agencies for both sponsorship and continuous monitoring.”
- Alliance for Digital Innovation, July 22, 2024
The challenges FedRAMP was facing were stark:
Nearly 90 cloud services were in the FedRAMP backlog for authorization while FedRAMP’s FY25 plan targeted completing only 50 authorizations.
Significant Change Requests were creating government-wide bottlenecks to access emerging technology and new features as a few overburdened agency security teams held up reviews and approvals.
New cloud services looking to enter the marketplace were confronted with a lack of agency sponsorship and an anticipated timeline of 2-3 years to complete the entire FedRAMP authorization process if they somehow managed to find a sponsor.
American Rescue Plan funding that had been used to supplement FedRAMP’s budget was spent, resulting in a decrease of FedRAMP’s budget right when it needed to grow the most; many of the March 2024 Roadmap items assumed a considerably expanded budget in future years.
Program authorization, an entirely new authorization path to replace the Joint Authorization Board (JAB) authorizations, needed to be built from scratch to scale with decreased funding.
FedRAMP had publicly committed to building its own cloud service to operate a government-wide Governance, Risk, and Compliance (GRC) platform and invested millions of dollars into a centralization strategy that seemed likely to fail due to budget constraints.
Cloud services with existing FedRAMP authorizations were overwhelmed by unreasonable continuous monitoring expectations, expensive and confusing Plans of Action & Milestones that created friction between providers and customers, and forced to build bespoke materials and reports for government customers that were often incorrectly treated as “federal information.”
FedRAMP requirements had effectively forced cloud services to create government-specific versions of their services that were less effective, lower quality, and more expensive than their commercial counterparts; nearly every service authorized in FY23 and FY24 was a government-focused offering instead of a commercial offering.
Building the Foundation in FY25
Government-wide programs like FedRAMP do not typically move quickly and the first half of FY25 was focused on consolidation, planning, and negotiation. A new governance structure for FedRAMP, a continuing resolution for funding, and external pressure to prioritize all of FedRAMP’s resources on a few cloud service providers who had been abandoned by the JAB needed to be absorbed, optimized, and directed. And a new understanding between OMB and GSA needed to be forged as everything about how the program would operate had changed.
By December, the overriding priority for FedRAMP was clear: clear the backlog. FedRAMP would not be able to build and implement a new program without solving this crisis, so nearly all resources available to the team would be refocused entirely on this one single problem for the rest of the year. The FedRAMP Board cleared the way for final review to focus on ensuring agencies had the information they needed for risk-based decision making instead of FedRAMP trying to eliminate all risk and the FedRAMP team deprioritized nearly all other activity to retask nearly its entire staff to addressing the backlog.
Then, under the direction of new leadership at GSA and OMB, FedRAMP began to develop an entirely new process for program authorization that would move FedRAMP from onerous paperwork-based traditional review to something cloud-native and built from the ground up for automation. A small team quietly developed the first prototype of what would become the 20x Key Security Indicators and, soon after, the initiative to build FedRAMP 20x was launched.
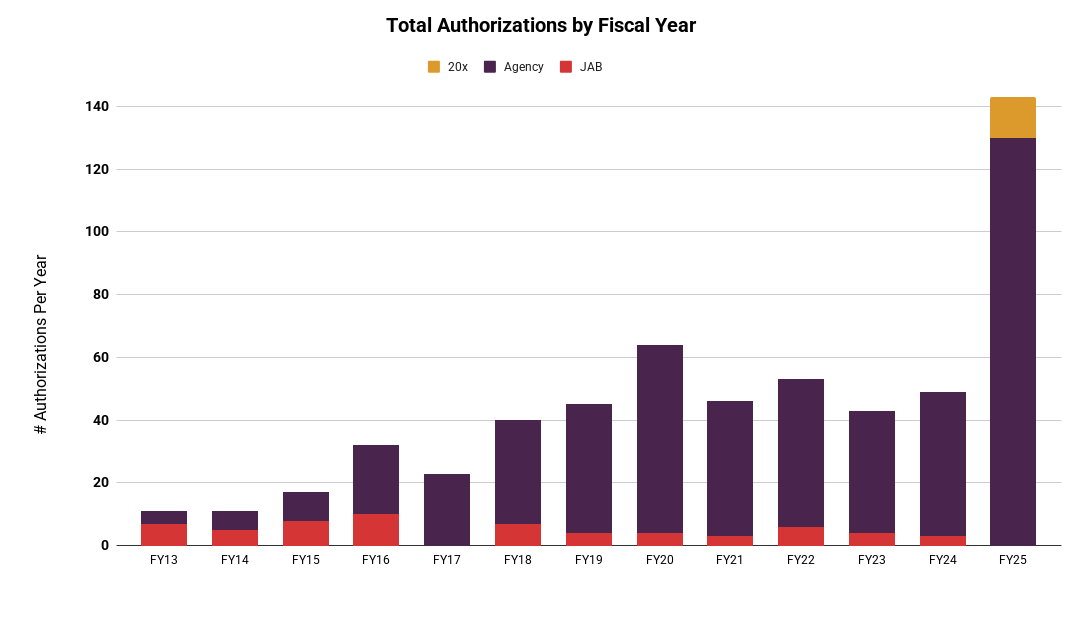
In the six months since, FedRAMP has remained laser focused on delivery: eliminating the traditional Rev5 backlog and reducing final review time to under 30 days, launching an initial 20x Phase One pilot to demonstrate interest in an automation-based assessment process, and publishing 18 requests for public comment on updated guidance in advance. We launched Community Working Groups including forums for public collaboration, increased transparency by publishing regular progress reports, met regularly with industry trade associations, and engaged with our community on social media. We saw that improved standards for FedRAMP 20x appealed to cloud services with existing Rev5-based authorizations and created the Balance Improvement Release (BIR) process to bring improvements over to existing authorizations in a careful, intentional manner.
And last week, right at the end of FY25, we announced that FedRAMP 20x Phase Two would launch at the beginning of FY26 to start the new fiscal year off hot. By the end of FY26 Q2, only a year after the initial announcement of the intent to build FedRAMP 20x, we anticipate a formal 20x authorization path will be open to the public that solves the majority of the problems underlying the traditional FedRAMP Rev5 path for Low and Moderate services.
| FY25 20x Metrics (since May 2025) | FY25 Rev5 Metrics (full FY) |
|---|---|
|
|
It’s Not All 20x
Nearly 500 companies have made significant investments in FedRAMP Rev5-based compliance while over 200 authorizing officials are using Rev5-based processes. These processes have significant flaws and must be adjusted carefully and intentionally to avoid expensive and unnecessary disruption while encouraging a rapid migration to more secure outcomes with improved communication and reduced friction for agencies and cloud services.
The Rev5 Balance Improvement Release (BIR) process will bring significant improvements from 20x to Rev5 during FY26 through a combination of closed beta tests, open beta tests, and optional wide release. The 20x improvements coming to Rev5 this year include:
Significant Change Notifications (SCN) will optionally replace the Significant Change Request process for Rev5. Currently transitioning to open beta, the SCN Balance Improvement Release solves one of the most critical issues with FedRAMP by allowing commercial services to operate their own business consistent with their authorized business practices while ensuring agency customers have sufficient information to understand how the service they authorized is changing.
- This improvement delivers on a specific demand from OMB in M-24-15 to “empower CSPs to deploy changes and fixes at their own pace, without requiring advance approval from FedRAMP or an authorizing official for individual changes to existing FedRAMP authorized products and services.”
The Minimum Assessment Standard (MAS) optionally replaces historically confusing FedRAMP boundary guidance, simplifying the scope of a cloud service offering to ensure that a FedRAMP authorization can be integrated properly into an agency information system boundary. The MAS limits the FedRAMP authorization to information resources that can directly impact customer information and clarifies the process for leveraging third-party services that are not FedRAMP Authorized. The MAS will soon enter open beta for Rev5.
- This improvement delivers on a specific demand in the FedRAMP Authorization Act to “establish and update guidance on the boundaries of FedRAMP authorization packages.”
The Authorization Data Sharing (ADS) standard allows cloud service providers to host FedRAMP authorization data in FedRAMP-compatible trust centers that directly integrate into their cloud service offering, share information with other customers, and simplify marketplace listing updates. This mechanism replaces an awkward government-operated cloud service for sharing data to move agencies towards the consumption of authorization data via automated mechanisms directly from cloud service providers in real time. The ADS is currently in closed beta for Rev5.
- This improvement delivers on specific demands from both M-24-15 and the FedRAMP Authorization Act to allow agencies to ingest machine-readable authorization data through automated means.
The Vulnerability Detection and Response (VDR) standard overhauls continuous monitoring expectations to focus on secure outcomes from real-world context-sensitive decisions about weaknesses and threats. The VDR requires persistently recurring detection of weaknesses at a much higher frequency and depth than traditional vulnerability scanning requirements, requires mitigation and remediation of high-risk weaknesses within time periods that are more appropriate for an AI-driven threat environment, and pushes industry towards the adoption of effective automated detection and response. The VDR is currently in closed beta for Rev5.
- This improvement delivers on specific demands from both M-24-15 and the FedRAMP Authorization Act to establish a modern framework for continuous monitoring that protects agencies from the most salient threats while avoiding promoting the separation of government and commercial services.
RFC-0015 on the Recommended Secure Configuration (RSC) standard proposes requirements and recommendations for cloud service providers to include critical information about configuring their cloud service securely, ship with secure defaults, and provide tools for agencies to easily audit and reset configurations to maximize security. The RSC will immediately enter open beta when formalized at the end of the public comment period.
- This improvement delivers on specific demands on Executive Order 14144 as amended by Executive Order 14306 to incentivize cloud service providers to produce specifications and recommendations for agency configuration of cloud services.
RFC-0016 on the Collaborative Continuous Monitoring (CCM) standard proposes new government-wide collaboration requirements and recommendations to reduce the burden of continuous monitoring on agencies and providers while ensuring agencies have automated access to the most critical data they need to make ongoing authorization decisions. The CCM will immediately enter open beta when formalized at the end of the public comment period.
- This improvement delivers on specific demands from both M-24-15 and the FedRAMP Authorization Act to allow agencies to ingest machine-readable continuous monitoring data through automated means, incentivize security through agility, and to provide a standard level of monitoring support government-wide.
These improvements together address significant historical flaws in the FedRAMP process and will push both cloud services and agencies towards a more effective continuous monitoring program government-wide over the next two years as both cloud service providers and agencies adopt the standards, tools, and capabilities necessary to meet these requirements and recommendations.
Delivering Adoption in FY26
Policies, beta tests, and pilots are just the foundation; in order to truly grow, a product needs widespread adoption which requires building with innovators to deliver off-the-shelf processes, workflows, and systems that stakeholders can easily use and deploy. FedRAMP worked fast in FY25 to lay the foundation so FY26 could concentrate on exactly that: wide release of better policies that will lead to widespread adoption in industry and government.
The goals for FY26 remain aggressive:
FY26 Q1: Complete the Phase Two pilot to finalize Moderate 20x authorizations and support initial government-wide adoption of critical AI services.
FY26 Q2: Open 20x Moderate and Low authorizations to the public with clear standards, early frameworks, and third-party tools that natively help cloud services and agencies adopt and deploy 20x.
FY26 Q3: Push wide-scale agency adoption and ensure all agencies have a path to adopt GRC automation tools that support 20x.
FY26 Q4: Open a 20x High pilot focused on hyperscale IaaS/PaaS to complete the new authorization path.
All of this heads toward a goal of retiring the Rev5 Low and Moderate agency authorization path by the middle of FY27 then for High by the end of FY27. In less than three years, FedRAMP intends to replace the entirety of FedRAMP as it existed at the beginning of FY25 with a true government-wide program that meets the demands of the FedRAMP Authorization Act and M-24-15.
And perhaps most importantly, our primary goal remains operating a process where qualified cloud services can receive a FedRAMP authorization within 30 days of submitting their authorization package to FedRAMP for review.
Risks and Managing Expectations
Delivering on bold goals requires incremental delivery, continuous improvement, and being willing to change schedules, expectations, needs, and plans based on changing requirements. FedRAMP has created a living Roadmap that is adaptable and updated on a biweekly basis to keep our stakeholders apprised of ongoing initiatives and work in the pipeline. As a forward-looking organization delivering policy like it’s a technology product, FedRAMP acknowledges that prioritizing the public delivery of working policy in small increments can create confusion and tension in a market that is used to waiting years for big changes then being given years to adopt them… but we’ve also seen powerful continuous feedback from industry that you would rather we work publicly and rapidly while risking changes to our plans than building in the dark over years to consistent timelines.
Unless that changes, FedRAMP will continue with the strategy of maximum transparency into our weekly plans, our short term strategy, and how all of this is affecting the overall multi-year plan. That includes transparency into staffing and ongoing risks.
The single biggest risk to FedRAMP today is our ability to hire and retain the qualified staff this program needs to be successful at scale.
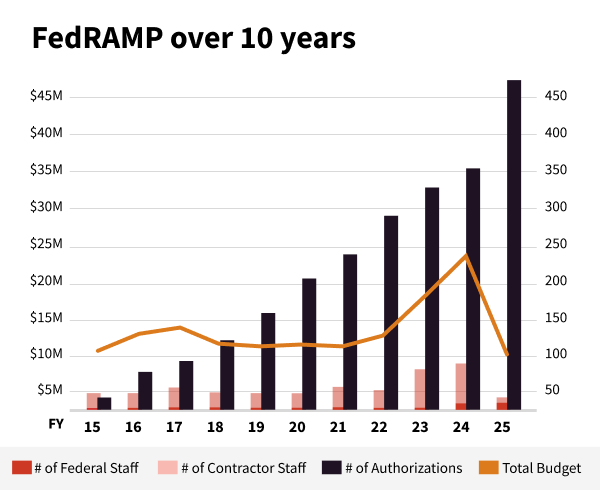
Our FY26 plans rely on hiring new staff to bolster our program authorization and continuous monitoring processes to relieve the burden on agencies and meet the massive demand for FedRAMP Authorized services in the marketplace. FedRAMP is entering FY26 with nearly ten open full time positions and a slightly smaller number of open positions on our only contract, but hiring is difficult in this environment. We’ll be looking for highly technical mission-driven individuals to join our team once the federal hiring freeze is lifted and hope many of you will consider joining us.
FedRAMP is Stronger Together
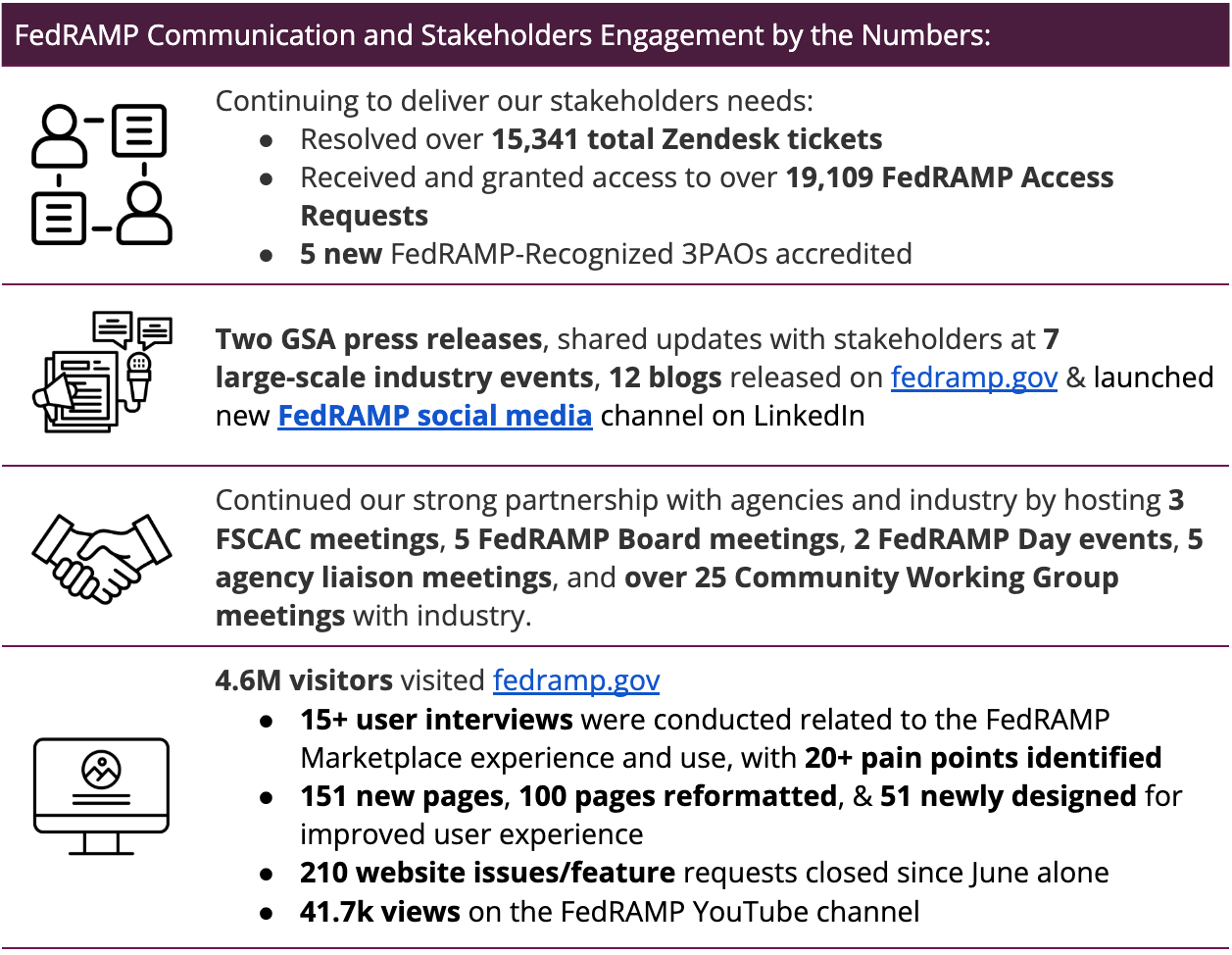
This program requires collaboration to succeed; the type of collaboration that is incredibly difficult for a government program. More than anything else in FY25, FedRAMP has demonstrated an ability to shatter the norms of government communication and engage directly with stakeholders in ways no one imagined possible.This central theme of FY25 must continue forward in FY26. FedRAMP will continue to work within the federal bureaucracy to double-down on the things that worked in FY25 and deliver new ways of working together in FY26:
Community Working Groups will continue to be the core of FedRAMP’s interaction with the public, supporting asynchronous discussions and Q\&A’s with monthly meetings on focused topics. Expect more organization and engagement in FY26 as we drive traffic from email queries to the GitHub discussion forums, spend more time planning meetings and preparing in advance, and continue to share everything along the way on YouTube for folks who can’t make it.
Government-wide quarterly FedRAMP Days will continue; we think everyone is hooked after hosting two of these. They are a lot of work, but bringing the entire government FedRAMP community together on a regular basis to focus on topics that matter to all of us just makes us stronger. And of course, moving our agency liaison meeting from a quarterly to monthly cadence will continue.
Our governance structure was mostly new for FY25 but unexpected changes affected the FedRAMP Board, our Technical Advisory Group, and the Federal Secure Cloud Advisory Committee. These changes have mostly been stabilized and we’re looking forward to active engagement with formalized members of all of these government partner bodies in FY26 - between all of these not many weeks will go by without some sort of active government partner meeting at FedRAMP.
Industry trade associations that actively support FedRAMP by organizing FedRAMP-focused events, responding to public comment, and treating FedRAMP like an active partner will continue to have priority access to the FedRAMP Director and team for honest updates at events and working sessions.
Podcasts and other long-form content will remain a priority for FedRAMP; we know that not everyone listens to these and they don’t necessarily have the reach of large conference speeches but the most important thing is that almost everyone who listens to a podcast about FedRAMP is guaranteed to be someone we want to talk to. We even have some thoughts about producing our own content for folks directly!
Social media, e-blasts, and blogs have been the simplest way to communicate updates out to the public in smaller chunks consistently each week and you can expect those to continue. If small regular updates are too much to keep track of we’ll make sure to keep our website’s Changelog updated as things change on that front too.
Requests for Comment may never feel routine but FedRAMP will continue to explore ways to ensure the public has the ability to help us make the right decisions in the right way. We opened public comment on over 20 different ideas in FY25, including 18 via our new RFC process, and every single thing we did was better off for it.
All of these activities are incredibly difficult and stressful for a small program focused on daily delivery of technical reviews and policy but collaboration remains the second most critical priority behind delivery.
And Then We Build
FY25 was a difficult and busy year for FedRAMP; FY26 will be a difficult and busy year for FedRAMP. We need to deliver a better assessment process, ensure everyone has the tools to leverage the resulting machine-readable information and processes, successfully influence government and industry to try something different, meet the demand for exponential growth, maintain strong partnerships with everyone involved, and chart a course through any potential disruption to ensure that the federal government can access and use modern technology with ease. Civil servants deserve the same access to modern cloud-based tools and services as everyone else. We can make that happen by building something better together, so that’s what we’re going to keep doing.