Focus on FedRAMP®
Discover what’s happening in the FedRAMP world.
FedRAMP 20x - Three Months In and Maximizing Innovation
Three months ago, FedRAMP launched 20x: the idea of a new approach to assessing and authorizing cloud services based on real security outcomes. Two months ago, FedRAMP released draft materials outlining how this approach might work. And one month ago,...
FedRAMP 20x - Two Months In and Taking Off
We’re sharing an inside look at FedRAMP’s progress again this month, in our second update on the ...
FedRAMP 20x - One Month In and Moving Fast
Exactly one month ago today GSA announced FedRAMP 20x, an initiative to rapidly modernize FedRAMP...
FedRAMP in 2025
Last year FedRAMP underwent a major overhaul after more than a decade. The biggest change took pl...
Focusing on Delivery
FedRAMP has shifted to a more aggressive cadence for releasing draft updates for policies and dir...
Exploring new ways to scale FedRAMP
For years now, federal agencies, companies, Congress, and a series of administrations have made c...
FedRAMP, Looking Back on 2024, Ahead to 2025
2024 has been a full year for FedRAMP, with changes large and small to the program and its team. ...
FedRAMP Help Center
Navigating the complex landscape of cloud security and FedRAMP requirements can be challenging fo...
FedRAMP Agile Delivery Pilot Update
FedRAMP is Moving Forward With Our Agile Delivery Pilot We have selected six Cloud Service Offer...
The Missing Piece of Our Modernization Puzzle&#...
FedRAMP’s vision for automated and data driven risk management has achieved a key milestone with ...
Digital Authorization Package Pilot Launch
Today, FedRAMP is launching the Digital Authorization Package pilot. This pilot will explore the ...
Welcoming a New Leader for a New FedRAMP
After an extensive search, FedRAMP is thrilled to welcome Pete Waterman as our new FedRAMP Direct...
Moving to One FedRAMP Authorization: An Upd...
We recently shared information about two key milestones for FedRAMP: the release of the FedRAMP m...
Strengthening the Use of Cryptography to Secure...
Today, FedRAMP is asking for public feedback on its proposed policy update to how we apply federa...
FedRAMP Metrics for Public Comment
Update: To ensure that we hear from as many voices and gather as much input as possible, we are e...
The Next Phase of FedRAMP
Today, the White House Office of Management and Budget (OMB) released M-24-15, “Modernizing the F...
FedRAMP's Roadmap Progress, One Quarter In
Earlier this year, we released FedRAMP’s 2024-25 roadmap, where we talked about our vision for th...
New Website Launch: automate.fedramp.gov
By Dave Waltermire FedRAMP’s Automation Website: A New Hub for Technical Documentation and Guida...
The FedRAMP Agile Delivery Pilot
By Ryan Palmer and Samuel Leestma Today, FedRAMP is launching a new pilot program, rooted in ite...
Release of Emerging Technology Prioritization F...
Today, FedRAMP is publishing the final Emerging Technology Prioritization Framework, with an init...
FedRAMP Governance
FedRAMP’s commitment to our customers is to make it safe and easy for the U.S. government to take...
A New Roadmap for FedRAMP
Today, the FedRAMP program is releasing a roadmap, to convey our strategic goals and how we’re pr...
RFQ for GRC Solution Released
The General Services Administration (GSA) and FedRAMP have issued a request for quotation (RFQ) (...
Penetration Test Guidance Public Comment Period
FedRAMP is seeking feedback on the draft FedRAMP Penetration Test Guidance. The original guidance...
Rev. 5 - Additional Documents Released
To modernize baselines, the National Institute of Standards and Technology (NIST) released the Sp...
Supplemental Direction v2 - CISA Emergency Dire...
Actions Required For Cloud Service Providers In consultation with the Joint Authorization Board (...
Supplemental Direction v1 - CISA Emergency Dire...
On Wednesday, January 31, 2024, the Department of Homeland Security (DHS) Cybersecurity and Infra...
FedRAMP's Emerging Technology Prioritization Fr...
The President signed Executive Order 14110 on Safe, Secure, and Trustworthy Development and Use o...
CISA Emergency Directive 24-01
On Friday, January 19, 2024, the Department of Homeland Security (DHS) Cybersecurity and Infrastr...
Modernization - Automating FedRAMP's Technology
As a reminder, you are invited to join FedRAMP’s monthly Office Hours session today at 11am ET We...
FedRAMP Modernization Overview
We are excited to share with you the concrete steps we are taking to upgrade technology and proce...
Extended Comment Period on Draft FedRAMP Memo
The Office of Management and Budget (OMB) extended the comment period for the Modernizing the Fed...
FedRAMP Repository - USDA Connect Update
As a reminder for all FedRAMP Office of Management and Budget (OMB) MAX system users, the reposit...
FedRAMP Policy Memo Public Engagement Forum wit...
The Office of Management and Budget (OMB) will be holding a virtual public engagement forum on We...
FedRAMP's Role In The AI Executive Order
On Monday, October 30, the White House issued an Executive Order (EO) on Safe, Secure, and Trustw...
OMB FedRAMP Memo
The Office of Management and Budget (OMB) has released a draft memorandum for Modernizing the Fed...
FedRAMP Repository - Next Steps
Starting mid-November, U.S. Department of Agriculture (USDA) Connect will be the repository solut...
A2LA Updates the R311
The American Association for Laboratory Accreditation (A2LA) recently released an updated version...
Rev. 5 - Additional Documents Released
FedRAMP has released the fourth wave of updated documents and templates to support the transition...
New 3PAO Training - Obligations and Performance...
FedRAMP recognized Third Party Assessment Organizations (3PAOs) now have a 300-0 Obligations and ...
CSPs Prioritized to Work with the JAB
The following Cloud Service Providers (CSPs) have been selected to work with the Joint Authorizat...
3PAO Assessment Teams Must Be Qualified
FedRAMP requires FedRAMP recognized third party assessment organization (3PAO) personnel, who per...
FedRAMP Guidance for M-21-31 and M-22-09
In accordance with Section 8 of Executive Order (EO) 14028 “Improving the Nation’s Cybersecurity”...
The Rev. 5 Approach to SC-8, and Protecting Dat...
The FedRAMP Program Management Office is driven to ensure the community understands the details a...
Rev. 5 - Additional Documents Released
The next wave of updated Rev. 5 documents has been released. This is the third wave of documents ...
Looking Ahead - FedRAMP PMO Communications Rega...
The FedRAMP Rev. 5 baselines have been released to correspond with updates to the National Instit...
FedRAMP Marketplace Upgrade
A new and improved FedRAMP Marketplace is here! The FedRAMP Marketplace provides a searchable and...
FedRAMP Guidance on BOD 23-02
The Cybersecurity and Infrastructure Security Agency (CISA) at the Department of Homeland Securit...
Updated Rev. 5 OSCAL Profiles and Resolved Prof...
FedRAMP has released the second wave of Rev. 5 documents: the Open Security Controls Assessment L...
Rev. 5 Baselines Have Been Approved and Released!
The FedRAMP Joint Authorization Board has approved the FedRAMP Rev. 5 baselines! The FedRAMP base...
GSA Releases FedRAMP’s 2023 Customer Survey
We want to hear from you! The FedRAMP PMO is asking for a few minutes of your time. Surveys give ...
GSA Administrator Appoints Members to the Feder...
The General Services Administration (GSA), in coordination with the Office of Management and Budg...
FedRAMP Authorizations Hit 300 Milestone
FedRAMP is excited to announce that we just reached a huge milestone: 300 FedRAMP Authorized Clou...
Updated FedRAMP 3PAO Obligations and Performanc...
The FedRAMP PMO, in coordination with the American Association for Laboratory Accreditation (A2LA...
CSPs Prioritized to Work with the JAB and Next ...
The following Cloud Service Providers (CSPs) have been selected to work with the Joint Authorizat...
Call for Federal Secure Cloud Advisory Committe...
Background The General Services Administration (GSA) is establishing the Federal Secure Cloud Adv...
FedRAMP FY22 Annual Survey Recap
The FedRAMP PMO would like to thank everyone who completed the FY22 Annual FedRAMP survey this Fa...
FedRAMP Announces the Passing of the FedRAMP Au...
The Federal Risk and Authorization Management Program (FedRAMP) has great news to share: The Pres...
Status of Crypto Modules in Historical Status
On July 1, 2022, many Federal Information Processing Standards 140 (FIPS 140) validated crypto mo...
Engaging with FedRAMP - PART 3, The SAR ...
FedRAMP often receives requests for information and guidance regarding the Agency Authorization p...
Engaging with FedRAMP - PART 2, The Kick...
FedRAMP often receives requests for information and guidance regarding the Agency Authorization p...
Engaging with FedRAMP - PART 1, The Inta...
FedRAMP often receives requests for information and guidance regarding the Agency Authorization p...
A Look Back at Fiscal Year 2022
FY22 was a year of achievement and progress for FedRAMP and we thank you for your collaboration. ...
CSP Prioritized to Work with the JAB and Next F...
The following Cloud Service Provider (CSP) has been selected to work with the Joint Authorization...
FedRAMP Agency Liaisons
FedRAMP’s Agency Liaisons are federal cloud security subject matter experts who serve as a crucia...
FedRAMP Announces Public Comment Period for Aut...
The FedRAMP PMO recently worked with the Joint Authorization Board (JAB) and the Office of Manage...
FedRAMP Releases Updated Brand Guide
The FedRAMP PMO is excited to announce the revised release of the FedRAMP Brand Guide! The update...
FedRAMP Launches OSCAL Developer Data Bites Series
FedRAMP is excited to launch an Open Security Controls Assessment Language (OSCAL) Developer Data...
FedRAMP Releases the FY22 Annual Survey
We want to hear from you! Please take a moment to complete the FedRAMP Annual Survey for Fiscal Y...
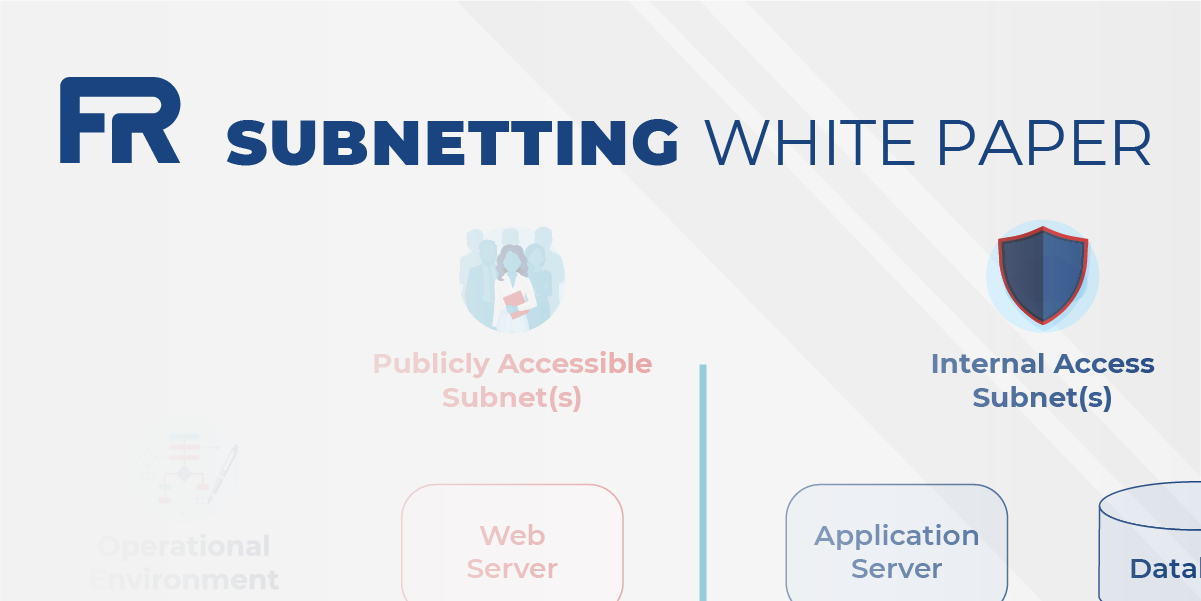
PMO Releases Subnetting White Paper
NIST control SC-7 for Boundary Protection relies in large part on subnetworks (subnets), specific...
Penetration Test Guidance Updates
We’re excited to announce the release of FedRAMP’s updated Penetration Test Guidance! These upda...
Update to the Plan of Actions and Milestones Te...
FedRAMP updated the Plan of Actions and Milestones (POA&M) template to include two new column...
CISA Releases Updated Cloud Security Technical ...
In response to Improving the Nation’s Cybersecurity Executive Order 14028 (EO), the Cybersecurity...
CSPs Prioritized to Work with the JAB and Next ...
The following Cloud Service Providers (CSPs) have been selected to work with the Joint Authorizat...
FedRAMP Receives First OSCAL System Security Plan
FedRAMP is excited to announce that the first Open Security Controls Assessment Language (OSCAL) ...
FedRAMP Rev. 5 Transition Update
At the end of 2020, National Institute of Standards and Technology’s (NIST) released Special Publ...
Responsibilities of CSPs and 3PAOs for FedRAMP ...
FedRAMP requires Cloud Service Providers (CSPs) to undergo an annual security assessment of their...
FedRAMP BOD 22-01 Guidance
The Cybersecurity and Infrastructure Security Agency (CISA) at the Department of Homeland Securit...
FedRAMP Prepares for 'Zero Trust' Stance
The growing threat of sophisticated cyber attacks has emphasized the importance of providing secu...
FedRAMP Updates the Threat-Based Methodology to...
FedRAMP updated the Threat-Based Methodology White Paper to reflect changes to our methodology be...
FedRAMP FY21 Annual Survey Recap
In August of 2021, the FedRAMP PMO released our annual customer feedback survey. Thank you to tho...
FedRAMP Connect Business Case Deadline Extended
The due date for FedRAMP Connect Business Cases has been extended to January 28, 2022 at 5:00 p.m...
FedRAMP Releases Updated CSP Authorization Play...
FedRAMP published an updated Cloud Service Providers (CSP) Authorization Playbook to provide CSPs...
Readiness Assessment Report (RAR) Templates and...
FedRAMP has updated the Readiness Assessment Report (RAR) Guide and templates (linked below) in o...
FedRAMP Publishes Draft Rev. 5 Baselines
FedRAMP is releasing baselines for public comment, and we want your feedback. Rev 5 Baselines F...
FedRAMP Turns 10!
Congratulations to the FedRAMP Community on our 10th year anniversary as a program! What a journe...
A2LA Updates the R346 Regarding Remote Baltimor...
The American Association for Laboratory Accreditation (A2LA), in conjunction with FedRAMP, decide...
Unique Vulnerability Counts with Container Scan...
As Cloud Service Providers (CSPs) start to submit their container vulnerability scans in order to...
A Look Back at Fiscal Year 2021
FY21 was a year of achievement and progress for FedRAMP and we thank you for your collaboration. ...
CSPs Prioritized to Work with the JAB and the N...
The following Cloud Service Providers (CSPs) have been selected to work with the Joint Authorizat...
FedRAMP Releases Updated Marketplace Designatio...
FedRAMP updated its Marketplace Designations for Cloud Service Providers (CSPs) guidance document...
FedRAMP Releases Updated Agency Authorization P...
FedRAMP recently released the updated Agency Authorization Playbook to better reflect how the ini...
The Importance of ATO Letter Submission
FedRAMP would like to remind federal agencies to authorize their Cloud Service Offerings (CSOs) a...
FedRAMP Updates CSP SSP (200A) Training
FedRAMP recently revised training materials for the System Security Plan (SSP) Required Documenta...
FedRAMP Releases OSCAL Validations
FedRAMP is excited to announce the development of OSCAL validations rules, which will allow FedRA...
FedRAMP Releases the FY21 Annual Survey!
We want to hear from you! Please take a moment to complete the FedRAMP Annual Survey and share yo...
FedRAMP Releases Updated OSCAL Template & Tools
In June 2021, FedRAMP announced NIST’s release of OSCAL 1.0.0 on GitHub for CSPs, 3PAOs, and agen...
Requesting Public Comment on FedRAMP Authorizat...
FedRAMP recognizes the importance of the FedRAMP Authorization Boundary Guidance in supporting th...
A2LA Updates the R311
In an effort to strengthen the qualifications of third party assessment organizations (3PAOs), th...
FedRAMP Announces NIST’s OSCAL 1.0.0 Release
NIST released version 1.0.0 of OSCAL . The FedRAMP PMO, in collaboration with NIST, is working to...
An Update to FedRAMP’s Low, Moderate, and High ...
The Federal Risk and Authorization Management Program (FedRAMP) provides standardized security re...
Remote Testing of Datacenters
Cloud Service Providers (CSPs) hire Third Party Assessment Organizations (3PAOs) to perform secur...
Rev5 Transition Update
FedRAMP uses the National Institute of Standards and Technology’s (NIST) guidelines and procedure...
FedRAMP Connect Business Case Deadline Extended
The due date for FedRAMP Connect Business Cases has been extended to May 21, 2021 at 5:00 p.m. ET...
Release of FedRAMP Incident Communications Proc...
The Federal Risk and Authorization Management Program (FedRAMP) recently updated the FedRAMP Inci...
JAB Guidance on CentOS Linux End of Life
Red Hat, the parent company of Community ENTerprise Linux Operating System (CentOS), has announce...
FedRAMP Launches YouTube Channel
The FedRAMP PMO recently launched the FedRAMP YouTube channel as a one-stop source for quick, sim...
Vulnerability Scanning Requirements for Containers
The Federal Risk and Authorization Management Program (FedRAMP) is pleased to announce the releas...
The New FedRAMP.gov
FedRAMP is excited to announce the launch of our revamped website. Thanks to feedback from our pa...
FedRAMP Explores a Threat-Based Methodology to ...
Feasibility Study: Agile Approach to Authorizations In 2017, the Office of American Innovation (...
CSPs Prioritized to Work with the JAB and Next ...
The following Cloud Service Providers (CSPs) have been selected to work with the Joint Authorizat...
FedRAMP Hosts a 3PAO Interact Week
Throughout the week of November 16, 2020, the FedRAMP PMO held a virtual, 3PAO Interact, to bring...
FedRAMP’s NIST Rev5 Transition Plan
FedRAMP uses the National Institute of Standards and Technology’s (NIST) guidelines and procedure...
CSPs Prioritized to Work with the JAB and Next ...
The following Cloud Service Providers (CSPs) have been selected to work with the Joint Authorizat...
FedRAMP Reaches 200 Authorizations
FedRAMP is excited to announce that we just reached a huge milestone: 200 FedRAMP Authorized Clou...
Updated 3PAO Obligations and Performance Standa...
FedRAMP recently updated the 3PAO Obligations and Performance Standards document to provide addit...
Additional FedRAMP OSCAL Resources and Templates
In June 2020, FedRAMP announced the release of OSCAL resources and templates on GitHub for CSPs, ...
Requesting Public Comment on Vulnerability Scan...
Technology changes rapidly and Cloud Service Providers (CSPs) continue to evolve in order to impr...
Please Take the FY20 FedRAMP Annual Survey!
FedRAMP is seeking your feedback in the FedRAMP Annual Survey. FedRAMP is constantly looking for ...
An Update to FedRAMP’s High Baseline SA-9(5) Co...
The Federal Risk and Authorization Management Program (FedRAMP) provides standardized security re...
FedRAMP Announces Document and Template Updates
FedRAMP released updates to the System Security Plan (SSP) Attachment 12 template, the FedRAMP Ma...
FedRAMP Announces Agency Liaison Program
The FedRAMP PMO recently kicked off a new initiative, the Agency Liaison Program, which is design...
Using the FedRAMP OSCAL Resources and Templates
The FedRAMP PMO, in collaboration with NIST, is working to digitize the authorization package thr...
Do Once, Use Many - How Agencies Can Reuse a Fe...
One of FedRAMP’s core value propositions is facilitating government-wide reuse of security packag...
JAB Prioritized CSPs and FedRAMP Connect Updates
The following Cloud Service Providers (CSPs) have been selected to work with the Joint Authorizat...
FedRAMP Lessons Learned for Small Businesses
The FedRAMP PMO is committed to helping small businesses and startups navigate the FedRAMP author...
FedRAMP Looks Back on a Successful FY2019
Fiscal Year 2019 was a year of achievement and progress for FedRAMP. Thank you for your collabora...
FedRAMP Moves to Automate the Authorization Pro...
FedRAMP is excited to announce that the program has reached an important automation milestone. Fe...
A Successful FedRAMP Startup & Small Business M...
On September 25, 2019 the FedRAMP PMO had its first Small Business/Start-Up Meetup in San Francis...
FedRAMP Connect Results and Next Round of Conne...
Congratulations to the following Cloud Service Providers (CSPs) selected to work with the Joint A...
FedRAMP Heads to San Francisco to Host Small Bu...
Are you a small business or startup interested in learning more about FedRAMP? The FedRAMP PMO is...
Please Take the FY19 FedRAMP Annual Survey!
The FedRAMP PMO is seeking your feedback and released the FedRAMP Annual Survey. If you’ve intera...
FedRAMP Launches Ideation Challenge
Do you have bold, innovative, and actionable ideas that can help transform the way agencies secur...
FedRAMP Marketplace Guidance Released
We receive thousands of questions through info@fedramp.gov, and one of the most popular topics is...
Get to Know FedRAMP's Program Manager of Securi...
As part of our spotlight series on the members of the FedRAMP PMO team, we wanted to introduce Jo...
Meet FedRAMP's Customer Success Manager
The FedRAMP PMO wants to give our readers a glimpse into the human side of the FedRAMP program by...
Best Practices for Multi-Agency Continuous Moni...
Both Cloud Service Providers (CSPs) and Federal Agencies play a role in Continuous Monitoring. Fe...
Reviewing the SAR - Best Practices for 3PAOs, A...
Cloud Service Providers (CSPs) pursuing a Low, Moderate, or High FedRAMP authorization are requir...
FedRAMP Updates 3PAO Requirements
Third Party Assessment Organizations (3PAOs) play a critical role within the Federal Risk and A...
Annual Assessment Guidance
The FedRAMP PMO recently encountered a question from a Cloud Service Provider (CSP) as to whether...
Impact of FedRAMP for Small Businesses
Did you know that over 30% of FedRAMP Cloud Service Providers (CSPs) are small businesses?* When ...
Understanding Baselines and Impact Levels in Fe...
The FedRAMP PMO fields a number of questions about impact levels and the security categorization ...







































































-Training_FRblog.png)